Niagara Module Signing
This article was imported from Niagara Resource Center.
Code signing is the process of applying a digital signature to a piece of code so that it can be later verified to ensure that it has not been modified after it was signed. This can help establish that the code came from a trusted source and reduce the risk of installing malicious code. In Niagara, all stock modules are signed and verified at runtime.
In Niagara 4.8 and later, there is added support for the signing and verification of third party modules. Third party module signing is still optional in most cases, but this will gradually shift to a requirement over the course of the next three releases.
For details on getting started with code signing, see “Code Signing” in the Niagara Developer Guide (Niagara 4.6 and later).
Verification modes
Niagara supports three different verification modes for third party modules. Module verification is based on the moduleVerificationMode, which can be configured to Low, Medium or High.
Each mode has the following behavior:
• Low — Any modules that are not signed or are signed with an untrusted or expired certificate will cause warnings but will still function normally. Errors will occur if a signed module is modified after it was signed and installation of such modules is not allowed.
• Medium — All modules must be signed by a valid, trusted certificate, but this certificate can be selfsigned. Installation of unsigned or invalidly signed modules is not allowed.
• High — All modules must be signed with a CA signed certificate. An internal CA can be used, but in this case, the CA certificate must be imported into the user trust store. Installation of modules signed with self-signed certificates is not allowed.
Staged roll-out
The module signing requirement will be enforced in stages. The planned roll-out schedule will span three releases with the following steps in each release.
• Niagara 4.8 — Default verification mode is Low.
• Niagara 4.9 — Default verification mode is Medium.
• Niagara 4.10+: Default verification mode is High.
New tools
In Niagara 4.8 and later, there are added Workbench tools to support module signing.
The Module Info View checks the signatures of modules installed on your local machine. The view lists the currently installed modules, each with a signature status icon.
The Jar Signer Tool is useful for non-developers or anyone using an unsigned legacy module that is no longer
supported by the vendor. The Jar Signer allows you to “sign” an unsigned *.jar file using a code signing certificate.
For more details, see “About Workbench tools” in Getting Started with Niagara.
Changes to existing tools
Several existing tools have been modified to accommodate module signing.
Software Manager/Commissioning Wizard
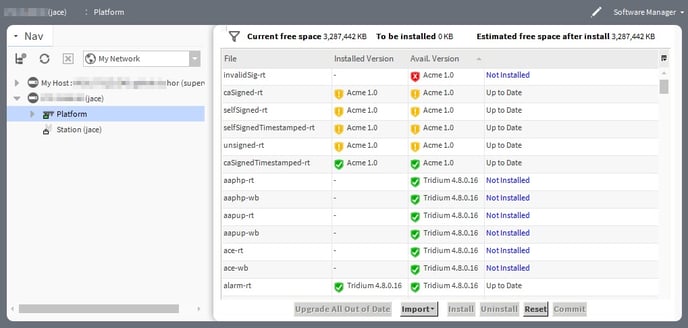
Both the Software Manager and Commissioning Wizard show an added icon in the Installed Version and Available Version columns indicating the signature status of the installed and available modules, as shown here.
NOTE: A red icon (![]() ) indicates the module has signature errors and cannot be installed (or if already installed locally, it cannot be loaded). A yellow icon (
) indicates the module has signature errors and cannot be installed (or if already installed locally, it cannot be loaded). A yellow icon (![]() ) indicates the module has signature warnings and should be installed with caution. A green icon (
) indicates the module has signature warnings and should be installed with caution. A green icon (![]() ) indicates that the module is validly signed. A gray “?” icon (
) indicates that the module is validly signed. A gray “?” icon (![]() ) indicates the module status is "unknown" which can be due to a couple of reasons. For details, see “Signature statuses” in this chapter.
) indicates the module status is "unknown" which can be due to a couple of reasons. For details, see “Signature statuses” in this chapter.
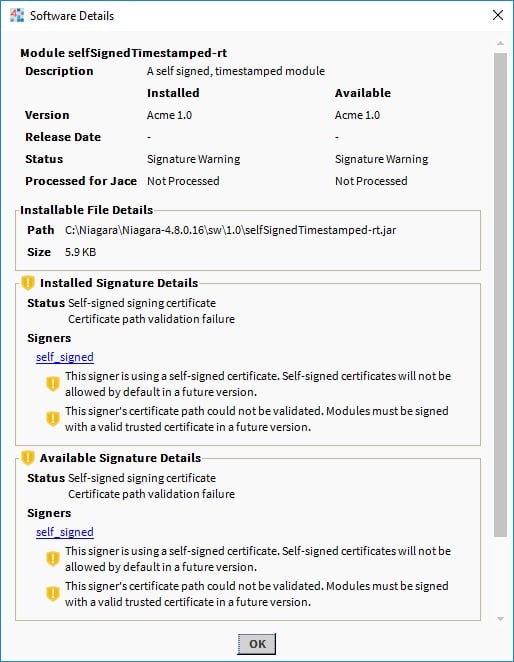
The Software Details window also includes signature status details for installed and available modules. This window displays all the signature statuses of the selected module with additional details. It will also provide a link to view the certificate that the module is signed with.
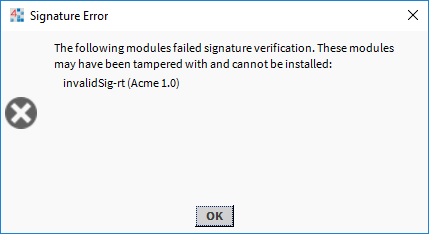
Attempting to install modules with signature warnings will cause a Signature Warning dialog to be displayed.

NOTE: Attempting to install modules with signature errors will cause the installation to fail.